Can I am done by you A favor? – Along With Other Present Card Fraud Tips
- February 23, 2021
- Best Friend Dating Site
- Posted by admin
- Leave your thoughts
whenever an easy demand from a trusted individual becomes fraudulence
Picture the scene : you can get a contact from your own employer or general asking if you’re able to assist them away. T hey occur to remotely be working if they require your assistance. They might desire you buying present cards for staff rewards or produce a purchase with the person because their card isn’t working . Fast ahead to t he scene that is final featur ing you out hundreds to thousands in your bank card, while the pretend boss or relative has accessed the cash from the present cards and gone quiet.
Cybercrime ‘s been around considering that the advent for the online, deploying techniques that be much more and much more complex. If it is Russian hackers utilizing spyware to take very nearly a million bucks in money from ATMs, or individuals using benefit of †peace sign ’ selfies to duplicate the fingerprint and get access to reports, there is certainly apparently no restriction towards the imagination and growing sophistication of cybercriminals.
Present cards are just one more black colored gap for protection specialists. The effects of these attacks have been known for years though significantly less reported on than credit card fraud. The Federal Trade Commission claims present cards are now actually the quantity one re payment way of scammers because they are impossible to trace.
More old-fashioned cybercrime strategies, such as targeted or untargeted phishing attacks, may also be used to get usage of card details en -masse. This kind of example dating included a gang that is criminal individuals impersonating HMRC, great britain income department, and coercing them into making re re re payments in iTunes present vouchers, that can be easily transported into money. The practices crooks used to exploit present cards are numerous because they are profitable.
Fraudsters are also recognized to remove present card figures at a shop and online check their balance
They start using it when they see that a dollar amount is loaded onto the card. The cloning of gift cards can be just as lucrative as the cloning of credit cards for the more technical-minded bad actors. Fraudsters can use credit cards stripe that is magnetic (easily obtainable to get online lawfully) to get use of the account amounts of present cards.
Right straight straight Back, a Brian Krebs investigation into Starbucks gift cards unearthed that it had been worryingly simple for fraudsters to empty customer’s bank reports through the feature that is auto-load. Starbucks commitment cards had been utilized to facilitate fraudulence on specific card holders, rather than on Starbucks by themselves. This scheme involved the card holder’s password, assisting the potential for further fraudulence become committed on a person if they reuse their passwords across numerous records.
The password/username model that features offered online users so “ well ” for a long time has become effortlessly compromised. Social engineering 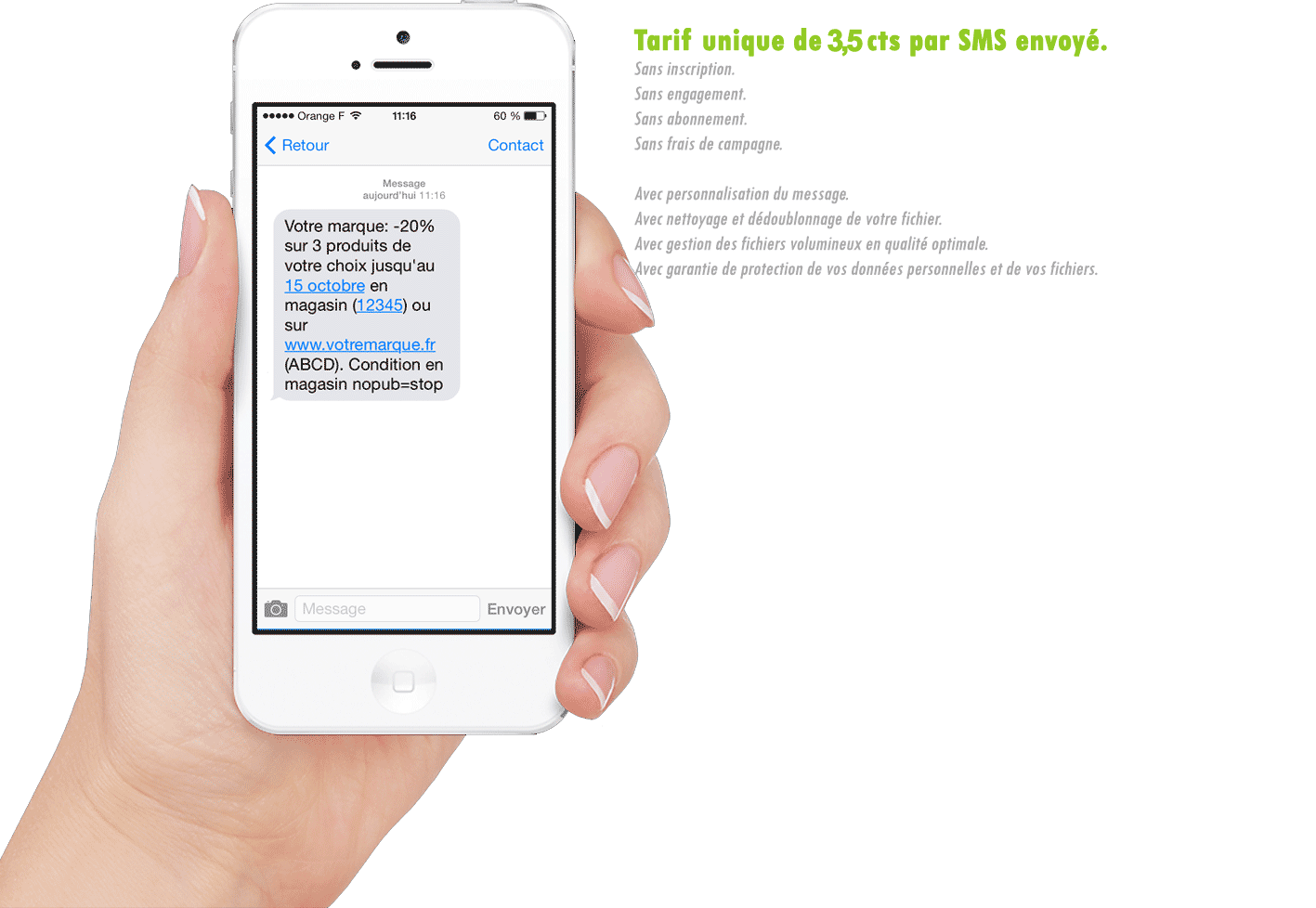 , credential reuse, and spyware have all been discovered with the capacity of bypassing it. We have to have a look at a multi-layered solution that includes technology that targets a user’s unique real relationship with a tool, such as for example passive biometrics.
, credential reuse, and spyware have all been discovered with the capacity of bypassing it. We have to have a look at a multi-layered solution that includes technology that targets a user’s unique real relationship with a tool, such as for example passive biometrics.
This technology can create a unique user impression that can’t be replicated by a cybercriminal by factoring in myriad of variables, ranging from patterns of behavior (where you access your accounts) right through to science fiction- esque analysis of how hard you hold your device or type. These methods represent the leading edge in fraudulence avoidance. By combining these with the original authentication that is two-factor, organizations can identify with near-certain precision whether a person is whom they state they’ve been. In a day and time where perhaps the many innocent of xmas gift suggestions is defrauded, adopting this brand new technology is an essential step of progress into the fight fraudulence.
Other measures stores may take in protecting clients from present card fraud consist of including PIN verification for their cards and maintaining them in a secure location out of the store floor, to end the card figures being accessed fraudulently. At precisely the same time, merchants can put up triggers as they could be reacting to a scam like our grandma from the beginning of this article if they see an individual purchasing an anomalous a number of gift cards.
A mixture of merchant diligence, customer understanding, and anti-fraud that is appropriate will help overturn this kind of fraudulence .

